What Changes Immediately After Installation
After installation, your PC becomes a locked-down, business-use system. The goal is to prevent risky behavior, malware, and downtime even if it means restricting things that are not business-related.
Here is exactly what changes:
- Infected or malicious websites are blocked
- Websites with bad or suspicious reputation are blocked
- Malware, ransomware, and viruses cannot run
- Non-business websites are restricted, including Gaming Websites (for example, xbox.com)
- Risky downloads and unauthorized software are blocked
These restrictions are intentional. They exist to prevent accidental clicks, unsafe browsing, and infections that commonly cause business disruption.
Note: Testing steps are provided as general guidance and may vary based on your organization’s security policies. If you’re unsure, our support team can assist.

How Your PC Will Behave Day-to-Day
Your computer will continue to function normally for business use, but some behavior will feel different especially at first.
Here’s what to expect:
- New applications may take 5–10 minutes to be allowed the first time they are installed
- Unknown or untrusted software will not run immediately
- Background security monitoring runs continuously without user interaction
- Most standard business software works normally without interruption
If something feels slower or delayed, it is usually because the system is verifying that the activity is safe before allowing it.
These checks typically happen only once per application and do not affect normal daily use.

Website Access & Web Filtering
Web access is controlled by site reputation and category, not just known threats.
- Adult and explicit content
- Gambling and betting websites
- Online games and gaming platforms
- Malware, phishing, and scam websites
- Sites with poor or unknown reputation
- Newly registered or untrusted domains

Application & Software Restrictions
Only approved and trusted applications are allowed to run.
- Unknown applications are blocked automatically
- Unauthorized tools cannot execute
- Malware cannot launch
- New applications do not run instantly
- Approval typically takes 5–10 minutes
- Some software may require manual review
This delay is expected and normal.
Malware, Virus & Ransomware Protection
Protection is always active.
- Malware is blocked automatically
- Ransomware is stopped before files are encrypted
- Suspicious files are quarantined
- No manual scans are required

Email, Downloads & File Handling
You should expect:
- Malicious email attachments to be blocked
- Dangerous downloads to be stopped before opening
- Files from untrusted sources to be quarantined
- Scripts and macros to be restricted
If something is blocked, it failed a security check.

Summary: What to Expect
After installation:
- Your system is secured and restricted
- Threats are blocked automatically
- Risk is significantly reduced
- Flexibility is intentionally limited
This tradeoff enables real protection instead of reactive alerts.


What to Expect
Security alerts will be sent via email when suspicious or blocked activity is detected
How to Test
- Testing Web Blocker or Anti-Virus is the easiest way to confirm email alerts are set up correctly.
- Confirm the correct alert email address is configured
- Verify the alert email is received
Expected Result:
You receive an alert email confirming the system is actively monitoring events

What to Expect
Malicious files are automatically detected and blocked or quarantined
How to Test
- Google “EICAR antivirus test file” — a universal, harmless test file from the European Institute for Computer Antivirus Research used to verify anti-virus protection
- Attempt to download or open the test file
Expected Result:
The file is blocked or quarantined, and an alert may be generated

What to Expect
Access to unsafe or non-compliant websites is blocked by category
How to Test
- Visit a gaming website such as xbox.com
- Gaming sites are commonly restricted by policy
Expected Result:
The site is blocked, and you may see a warning or block page

What to Expect
Sensitive data is encrypted according to your organization’s security policy
How to Test
- For Windows: Search “BitLocker” in the Start menu and check the drive encryption status.
- For macOS: Open System Settings → Privacy & Security → FileVault to confirm encryption is enabled.
Note:
Encryption testing is environment-specific
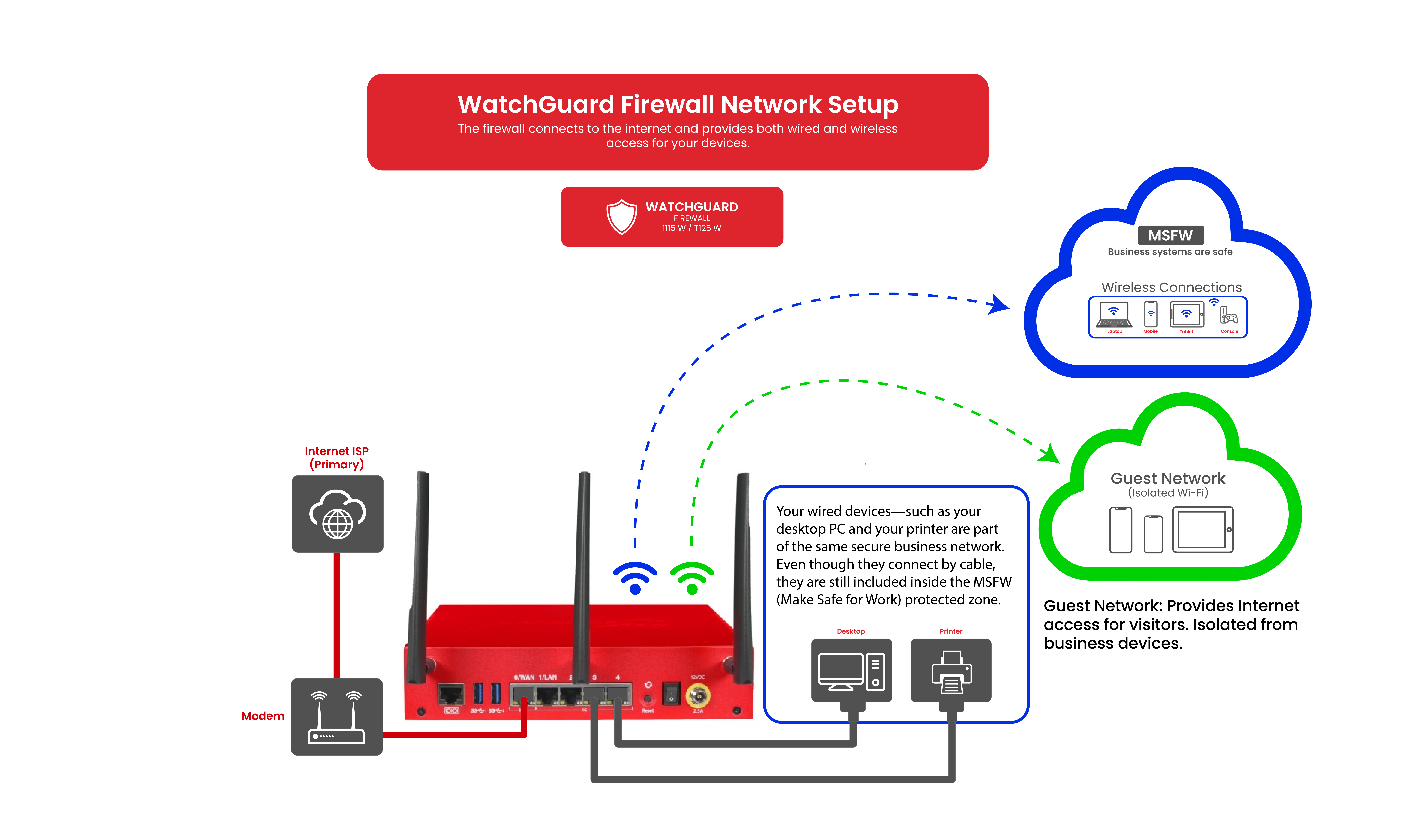
Hardware Firewall (If Installed)
This section applies only to deployments that include a hardware firewall.

What to Expect
Certain websites, services, or applications may be restricted based on security or usage policies.
How to Test
- Attempt to access a website or service known to be blocked
Expected Result:
Access is Denied

What to Expect
Traffic from specific countries or regions is restricted to reduce risk from high-risk locations.
How to Test
- Attempt to visit a website hosted in a blocked region
- Example: A Russian consulate website (.ru domain)
Expected Result:
The site is blocked due to geographic restrictions

What to Expect
The firewall monitors for suspicious outbound connections that may indicate malware or botnet activity.
How to Test
- This feature runs automatically in the background
Expected Result:
Suspicious outbound traffic is automatically blocked

Tor Network Blocking
What to Expect
Connections to and from the Tor network are blocked to prevent anonymous or high-risk traffic.
How to Test
- Visit a known Tor test or Tor access site (support can provide examples)
Expected Result:
Access is blocked
Security Best Practices & Reminders
To maintain a secure environment:
- Use strong, unique passwords
- Do not share login credentials
- Keep devices locked when unattended
- Report unexpected behavior immediately

If anything doesn’t behave as expected:
- Recheck the steps above
- Confirm installation completed successfully
- Contact support for assistance
Our team is happy to assist and verify your setup.