BUSINESS ENDPOINT COVERAGE
Web Blocker
Web Blocker prevents access to malicious, phishing, and high-risk websites by analyzing web traffic in real time. It protects users from common web-based threats while improving productivity.
- Blocks malicious and phishing websites
- Prevents drive-by downloads
- Enforces safe browsing policies
- Uses continuously updated threat intelligence

Full Encryption ensures that sensitive data stored on devices remains protected, even if a device is lost or stolen.
- Encrypts data at rest
- Protects business and user data
- Prevents unauthorized data access
- Supports compliance requirements

Zero Trust Security follows a multi-step classification process. Each stage filters out threats faster, more accurately, and with minimal disruption to your users. The zero trust application security model comprises of following key functionalities.
- Already Known Programs
- Easily Detected Malware
- Machine Learning
- Human Expertise

Ransomware Protection
Ransomware Protection detects suspicious behavior and blocks ransomware attacks before files and systems can be encrypted.
- Detects ransomware activity
- Prevents unauthorized encryption
- Reduces downtime and data loss
- Adds protection beyond traditional antivirus

Patch Management automatically identifies missing or outdated patches and keeps systems secure against known vulnerabilities.
- Automates patch deployment
- Reduces vulnerability exposure
- Keeps systems up to date
- Improves overall security hygiene

ThreatSync correlates security events across endpoints, firewalls, and network layers into a single, unified view.
- Centralizes threat visibility
- Reduces alert fatigue
- Improves detection accuracy
- Accelerates incident response

EXECUTIVE ENDPOINT COVERAGE
Human + AI SOC combines automated intelligence with real security professionals to monitor and respond to threats 24/7.
- 24/7 threat monitoring
- AI-powered detection
- Human-led incident investigation
- Rapid response and containment

Compliance Coverage supports organizations in aligning their security controls with regulatory and industry standards.
- Aligns security controls with compliance needs
- Improves audit readiness
- Reduces compliance gaps
- Strengthens governance

ESSENTIAL SECURITY
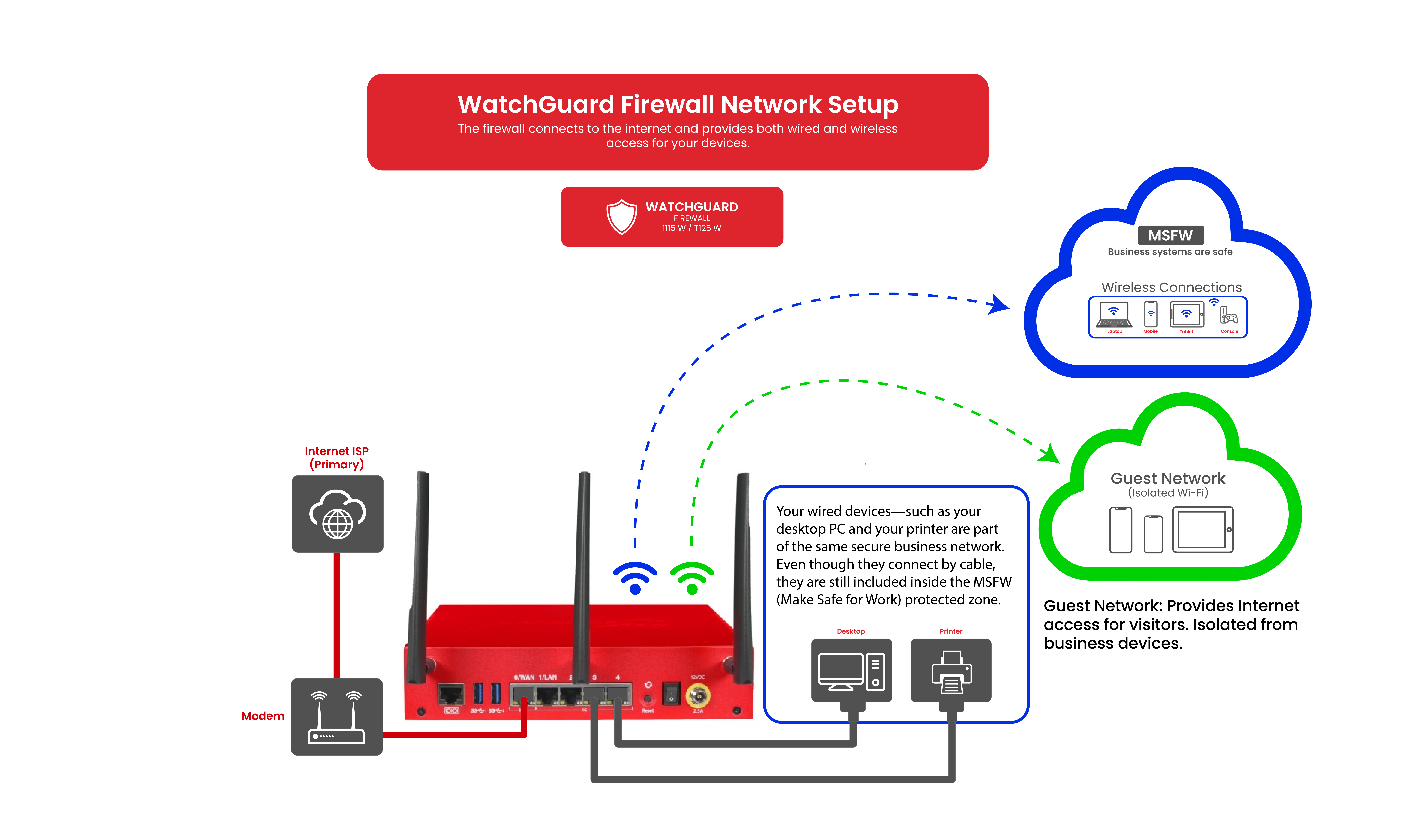
We provide right-sized hardware firewall appliances based on the number of protected devices:
- 1–4 devices: T115W hardware firewall
- 5–20 devices: T125W hardware firewall
- 21–24 devices: T145W hardware firewall
- 25+ devices: Custom deployment — please contact us for a tailored solution

APT Blocker
APT Blocker protects against advanced persistent threats designed to evade traditional security solutions.
- Detects stealthy attack patterns
- Blocks command-and-control traffic
- Prevents lateral movement
- Defends against targeted attacks

Advanced Antivirus
Advanced Antivirus uses behavioral and signature-based detection to stop known and unknown malware threats.
- Real-time malware protection
- Detects zero-day threats
- Minimal performance impact
- Continuous updates

Application Filtering
Application Filtering allows administrators to control which applications can operate on the network.
- Blocks unauthorized applications
- Controls application-level traffic
- Improves bandwidth usage
- Reduces attack surface

Geo Filtering
Geo Filtering allows or blocks traffic based on geographic location to reduce exposure to high-risk regions.
- Restricts traffic by country or region
- Reduces global attack exposure
- Enforces access policies
- Enhances network security

Botnet Protection
Botnet Protection prevents infected devices from communicating with known botnet command servers.
- Blocks botnet communications
- Prevents data exfiltration
- Identifies compromised devices
- Uses real-time threat intelligence

Tor Exit Node Blocking
Blocks traffic from Tor exit nodes to prevent anonymous and potentially malicious access attempts.
- Prevents anonymized attacks
- Improves traceability
- Strengthens perimeter defenses

ThreatSync Automation
ThreatSync Automation enables automatic actions in response to detected security threats.
- Automates threat containment
- Reduces response time
- Minimizes manual intervention
- Ensures consistent security actions

ThreatSync+
ThreatSync+ enhances ThreatSync with advanced analytics, deeper threat intelligence, and proactive detection capabilities.
- Advanced threat correlation
- Enhanced analytics and insights
- Proactive threat identification
- Enterprise-grade visibility

PREMIUM SECURITY
Compliance Guidance
Compliance Guidance provides actionable recommendations to help organizations maintain and improve compliance.
- Provides compliance best practices
- Guides security improvements
- Reduces audit complexity
- Supports regulatory alignment

Full Compliance Reporting
Full Compliance Reporting delivers detailed security and compliance reports to support audits and regulatory requirements.
- Generates audit-ready reports
- Improves visibility and accountability
- Simplifies compliance documentation
- Supports ongoing governance