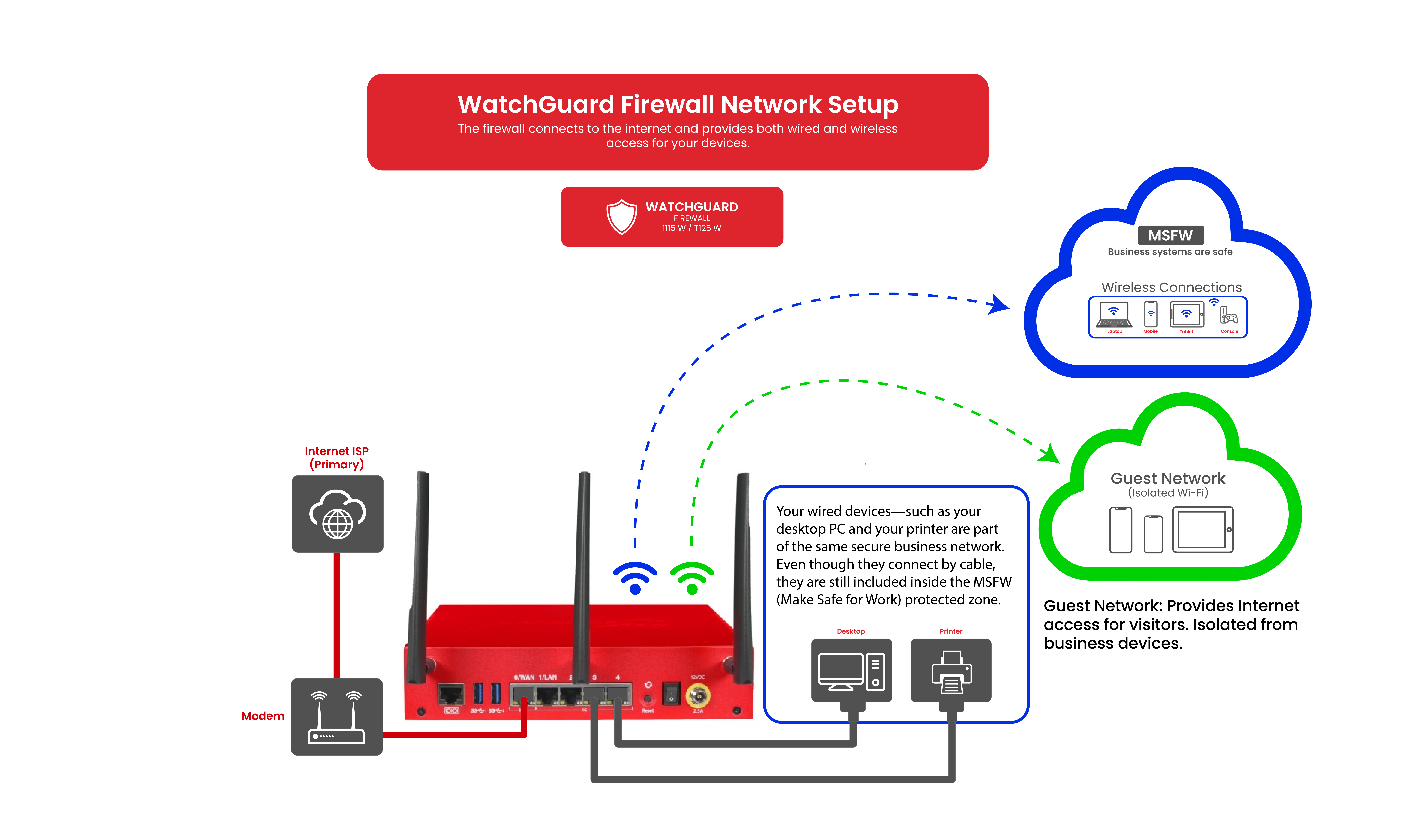
How Does Zero Trust Application Security Work
The Zero Trust model used by WatchGuard Zero Trust Security follows a multi-step classification process. Each stage filters out threats faster, more accurately, and with minimal disruption to your users. The zero trust application security model comprises of following key functionalities.
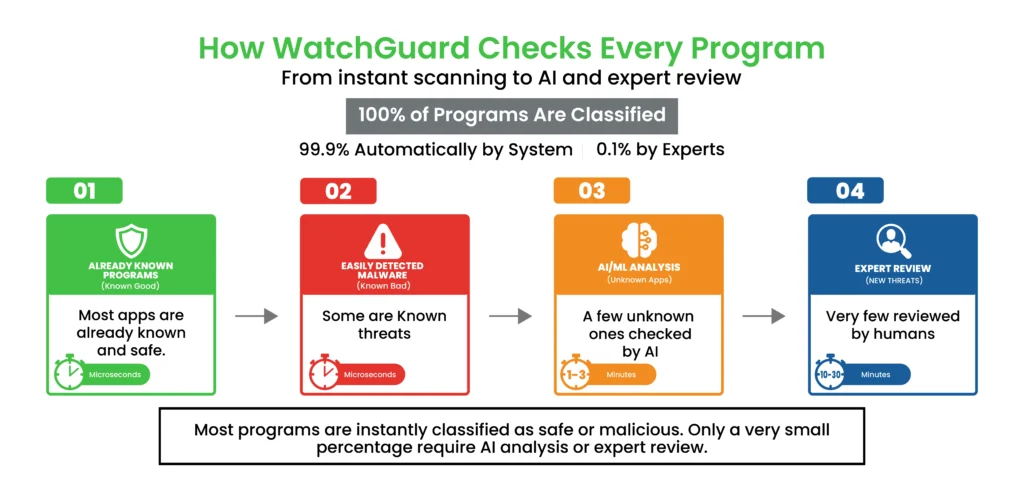
Already Known Programs:
The instant a file matches this ever-growing library of more than three billion vetted apps, it’s ready to go. If the app is unknown, it is submitted for review, with three more stages to go.
Easily Detected Malware:
An enormous intelligence network with over two billion qualified malware samples and known attacks provides a quick way to quarrantine malware that tries to get installed. If an application is not a known good or easily detectable bad, it is submitted to further investigation.
Machine Learning:
But what about those files in between, not clearly safe, not clearly malicious? That’s where sophisticated machine learning is used. Those pieces of software learn about behavior, code constructs, and digital signatures to reveal threats no one has ever seen before. Its AI feature of machine learning in cybersecurity enables automated application classification and verification so that safe and clean applications run smoothly without any interruption.
Human Expertise:
And when machines hit their limits, the best cybersecurity experts take over. They examine edge cases, optimize threat data, and instruct the system to learn from each interaction. This mix of automation and human expertise renders WatchGuard Zero Trust Securitynot just reactive, but conscientiously adaptive.
Real-Time Continuous Threat Monitoring and Learning
Threats are constantly evolving, not just on a yearly basis. That’s why WatchGuard Zero Trust Security continues to monitor activities even after initial classification. If a file behaves differently or any suspicious activity arises, the system re-assesses it right away. The continuous threat monitoring helps in application classification and verification based on attack patterns and signatures.
This ongoing feedback process helps to keep the trusted programs from turning rogue and outwits the attackers from getting in by penetrating through updates or system modifications. Your business remains secure while Varpath handles the process without having to monitor it daily manually.

Benefits of WatchGuard Zero Trust Application Security
- Full visibility using WatchGuard Advanced EPDR into every application installed and used.
- Fewer false alarms, so your team can focus on real threats, not noise.
- Faster reaction time due to WatchGuard machine learning.
- Human expertise that strengthens AI accuracy.

Why Zero Trust Application Security Matters
Cybercriminals are striving hard to remain undetected against zero trust endpoint protection and they have honed their strategy and currently merge with known surroundings, snatching little windows of chance and waiting for the right moment to act. WatchGuard Zero Trust Security successfully prevents this possibility by eliminating default trust entirely.
The zero trust application security methodology aligns with typical models such as NIST and CISA, which adopt ongoing verification as core security practice. Under these guidelines, Varpath guarantees your systems are secure, compliant, and transparent.
Collective Real-Time Application Protection
Each new file scanned by WatchGuard Zero Trust Security contributes to an increasing global threat database. This shared intelligence enhances your security in real time. The more organizations that have the system, the quicker it is, the more intelligent it is, and the more effective it is at catching new threats before they can propagate.
That is the power of an interconnected defense system, which becomes more powerful for all as it learns to counter attacks being waged everywhere on the globe.

Smarter Protection Starts with Zero Trust Application Security
WatchGuard Zero Trust Security is not a product so much as an adaptive model of security that responds dynamically to your own particular situation and the ever-shifting threat landscape. Varpath brings this intelligence to life by delivering expert management, around-the-clock monitoring, and strategic integration across all of your systems. Learn how embracing a Zero Trust Endpoint Protection strategy can revolutionize the way your organization does cybersecurity.

FAQs
Frequently Asked Questions
What does WatchGuard Zero Trust Security actually do?
It performs continuous threat monitoring and constantly checks every process, file, and application before letting it run. Nothing is trusted by default, which means hidden or unfamiliar software can’t slip through unnoticed.
How is WatchGuard Zero Trust Security different from traditional antivirus?
Traditional tools rely on signatures of known threats. WatchGuard Zero Trust Security combines application allow list and deny list, application classification and verification, machine learning, and expert review to detect new, unknown, or modified malware before it acts.
Does WatchGuard Zero Trust Security slow down systems?
No, application classification and verification happen in real time through cloud processing and lightweight endpoint agents, so performance remains stable while protection runs quietly in the background.
Can it work alongside other endpoint protection tools?
Yes. It integrates directly with WatchGuard Advanced EPDR and can coexist with most enterprise-grade security layers managed by Varpath.
How often are the threat lists and AI models updated?
Updates are continuous. The platform learns from global threat data gathered across all WatchGuard endpoints, improving accuracy every time a new file is analyzed.
Is WatchGuard Zero Trust Security compliant with industry regulations?
Yes. It supports data-protection standards such as NIST, CISA, HIPAA, and GDPR by enforcing constant verification and detailed activity logging.
What happens when a file is flagged as suspicious?
The system’s Zero Trust Endpoint Protection isolates it immediately. Machine learning examines its behavior, and if needed, human analysts step in to verify and reclassify the file safely.
How does Varpath support organizations using Zero Trust Security?
Varpath configures policies, monitors every classification, handles reporting, and ensures WatchGuard Zero Trust Security runs flawlessly across all endpoints giving businesses continuous protection with zero guesswork.